In a move that has sent ripples through the cybersecurity community and the social media landscape, X (formerly Twitter) officially integrated Account IP Location displays globally in late 2025.
For years, the industry focus was on Content Moderation—the Herculean task of policing what is said. However, as generative AI makes “fake content” indistinguishable from reality, the battlefield has shifted. The new frontier is Identity Governance: proving not just what was said, but the geographic and technical origin of the voice.
While some view this as a blow to privacy, X’s leadership frames it as a “strategic patch” for the global town square. But can a simple IP tag truly stop a sophisticated botnet?
How X’s IP Location Feature Works?
X’s implementation is deliberately understated:
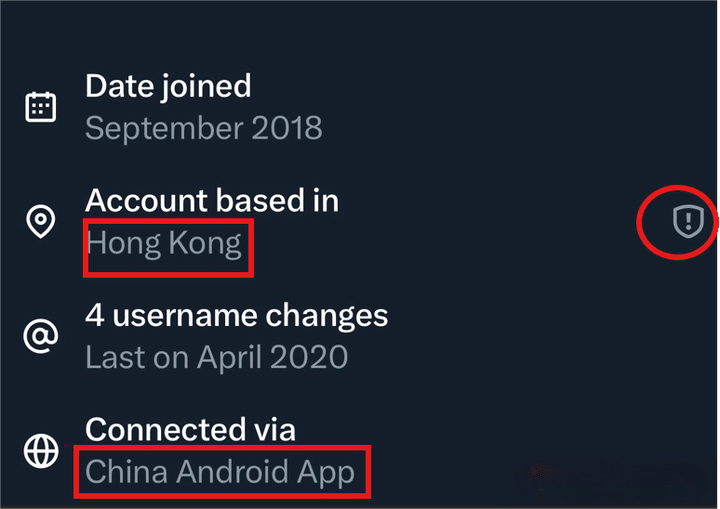
Location: The IP-derived location is not shown prominently under every post or reply. Users must visit a profile → tap “View more info” to see it. By default, it displays only the country, with an option to show just the continent.
Data source: X explicitly states it uses a combination of registration location and recent login activity—not real-time IP. Travel, VPNs, and proxies can cause mismatches, and the platform notes that the displayed location may be inaccurate or outdated.
This contrasts sharply with approaches seen on some other major platforms (particularly in China since 2022), where IP location is displayed directly under posts and comments in near-real time, making it highly visible to all users.
How IP Transparency Filters High-Volume Automation
The real power of IP location display lies not in advanced detection, but in raising the cost of basic deception.
Immediate impact on low-end manipulation
- Domestic “astroturfing” operations pretending to be overseas voices
- Crude bot farms using datacenter proxies
- Cross-border influence accounts masquerading as local users
- Bulk review/engagement farming from obvious IP clusters
These tactics become instantly visible when dozens of “American” accounts all show IPs from the same foreign city.
Higher operational costs for bad actors
- Cheap datacenter proxies (~$2/IP pools) become largely useless.
- Operators must shift to expensive residential proxies (often 5–10× more costly).
- Rapid account switching or bulk registration becomes riskier and slower—abnormal IP patterns stand out.
Better signal for users, researchers, and regulators
- Journalists and OSINT analysts can quickly spot coordinated inauthentic behavior.
- Governments monitoring foreign influence campaigns gain a new public data point.
- Ordinary users get a subtle cue when an account’s claimed identity doesn’t match its apparent origin.
In short, the feature doesn’t eliminate manipulation—it makes low-effort, high-volume manipulation much harder.
Limitations of IP Transparency: Why IP Location Alone Fails Against Sophisticated Bot and Fraud Attacks
IP location transparency is often seen as a simple way to improve platform security, but IP-based signals alone cannot defend against modern bot attacks and automated fraud. While IP information can help identify basic anomalies, it provides limited insight into whether a user is legitimate. Advanced attackers deliberately exploit this limitation by adopting infrastructures designed to evade IP-based detection.
Effective user verification requires a layered security approach that combines IP intelligence, device fingerprinting, and behavioral analysis. Without these additional signals, IP transparency quickly becomes ineffective against sophisticated automation.
Why IP-based detection fails against advanced attack infrastructures?
Residential proxies enable bots to appear as real users
Residential proxy networks route traffic through real household broadband connections distributed across different regions. Because these IPs belong to genuine home users, the traffic appears natural in both location and network characteristics. This makes residential proxies particularly effective for bot traffic, account takeover attempts, and large-scale fraud that rely on blending in with legitimate users.
Cloud phone clusters replicate real mobile behavior at scale
Cloud phones allow attackers to generate thousands of virtual mobile devices that can be automated, reset, and assigned different IP addresses. Each device mimics real smartphones, making the traffic extremely difficult to detect using IP location alone. Cloud phone infrastructure is widely used for mobile fraud, fake engagement, and coordinated bot campaigns targeting apps and platforms.
Mobile SIM pools bypass IP location checks entirely
SIM pools use real SIM cards connected to legitimate mobile carrier networks, producing traffic with fully valid IP locations. With the ability to rotate hundreds of SIM cards, these systems generate large volumes of automated activity that appear indistinguishable from real mobile users in IP-based security models.
Why modern bot protection requires more than IP transparency?
IP location should be treated as a contextual signal rather than a core verification mechanism. IP addresses are easy to rotate, mask, or spoof through proxies, VPNs, and mobile networks, making them inherently unreliable as a standalone defense.
A resilient bot management and fraud prevention strategy is built on three complementary layers:
IP intelligence as a weak signal
IP data provides geographic and network context but is highly unstable and easily manipulated. It supports risk scoring but cannot determine authenticity.
Device fingerprinting as a strong identifier
Device fingerprinting identifies the underlying device using browser attributes, operating system characteristics, hardware and screen parameters, environment variables, detection of cloud phones or virtual machines, and device consistency across accounts. This layer is essential for detecting automation, account abuse, and multi-account fraud.
Behavioral analysis as the human verification layer
Behavioral signals analyze how users interact with a site or application, including mouse movement patterns, interaction timing, page dwell time, navigation behavior, and AI-based human–bot differentiation. This is why CAPTCHA-based challenges and behavioral verification remain fundamental to modern bot protection solutions.
By integrating IP intelligence with device fingerprinting and behavioral analysis, GeeTest CAPTCHA delivers adaptive bot management that goes beyond IP transparency. This layered approach enables platforms to stop sophisticated bot and fraud attacks while maintaining a seamless experience for legitimate users.
Conclusion
The rollout of IP location display on X signals a broader shift in social media governance from managing content to understanding identity context. By increasing transparency around where accounts appear to originate, platforms raise the baseline cost of abuse and make low-effort manipulation more visible.
At the same time, IP location alone is not a security solution. Advanced actors will continue to bypass single signal defenses using increasingly sophisticated infrastructure. Sustainable governance depends on layered identity assessment that combines IP context, device intelligence, and behavioral analysis.
In this sense, IP location display is not an endpoint but a starting point. It represents an early step toward more transparent, resilient, and accountable digital platforms in an environment shaped by automation and global scale.