Automated abuse is no longer driven by noisy, short lived datacenter bots. Today, many of the most damaging attacks are carried out through infrastructure that closely resembles real users. Static residential proxies sit at the center of this shift.
By combining the credibility of residential IP addresses with long term IP persistence, static residential proxies allow automated tools to blend into normal traffic, maintain sessions, and build trust over time. For enterprise security teams, this makes traditional IP based defenses increasingly unreliable.
This article provides a comprehensive explanation of what static residential proxies are, how they operate, how they differ from other proxy models, and why they represent a critical challenge for modern bot detection, fraud prevention, and account security.
Definition and core characteristics of static residential proxies
A static residential proxy is a proxy service that provides a fixed IP address assigned to a real residential network. Unlike rotating proxies that change IPs frequently, a static residential proxy keeps the same IP over an extended period, sometimes for weeks or months.
Because the IP originates from an internet service provider that serves households, traffic routed through it appears similar to that of a genuine home user. This combination of residential origin and IP persistence makes static residential proxies significantly more difficult to identify using basic IP reputation or blacklist-based controls.
Key characteristics include IP stability, residential attribution, long session duration, and higher trust scores compared to datacenter IPs.
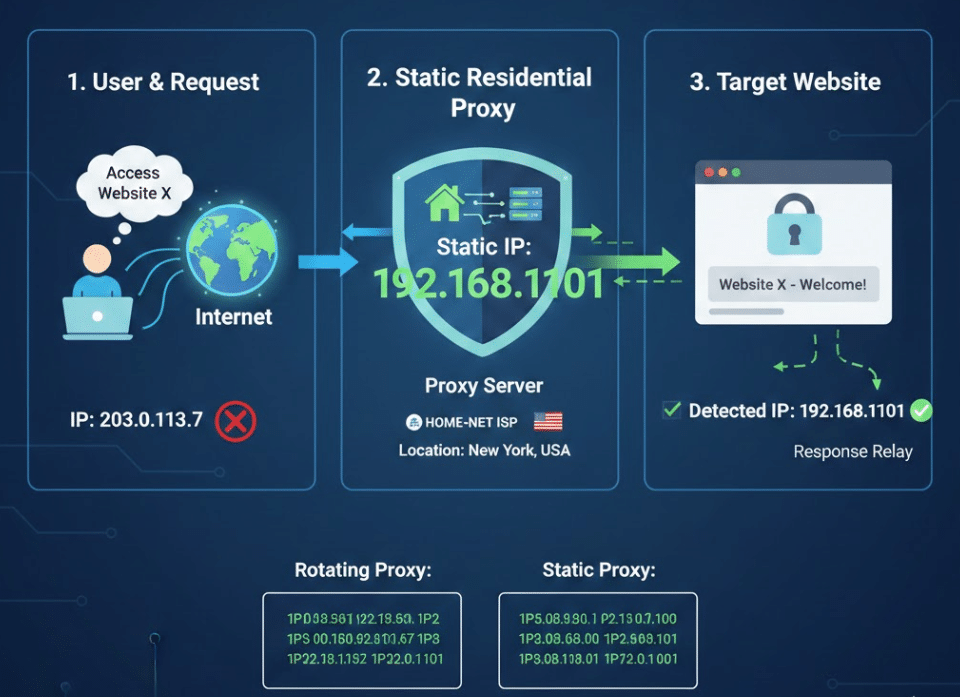
How Static Residential Proxies Work
Static residential proxies, often called ISP proxies, are a specialized hybrid in the proxy world. They combine the high trust of a residential IP address with the high speed of a datacenter.
Unlike rotating residential proxies, which change your IP address frequently, a static residential proxy gives you a permanent, unchanging IP that belongs to a legitimate Internet Service Provider (ISP) like AT&T, Verizon, or Comcast.
How the Technology Works
The core functionality of a static residential proxy lies in how it is sourced and hosted.
- Sourcing the IP: A proxy provider contracts directly with an ISP to lease a range of IP addresses. These IPs are categorized in the regional Internet registry as “Residential,” exactly like the one you use at home.
- Hosting in a Datacenter: Instead of routing traffic through a physical home device, these IPs are assigned to high powered servers in a datacenter.
- The Connection Path: * Your Request: You send a request, such as logging into a social media account.
- The Proxy Server: The request hits the datacenter server.
- The Mask: The server replaces your real IP with the leased residential IP.
- The Target Website: The website checks the IP and sees it is registered to a household ISP rather than a server farm. Because the IP does not change, the website assumes you are a consistent human use
Comparison: Static Residential vs. Data Center vs. Rotating Residential
To understand why Static Residential Proxies are premium (and expensive), we must compare them to the alternatives.
| Feature | Datacenter Proxies | Rotating Residential Proxies | Static Residential (ISP) Proxies |
| IP Origin | Server farms in data centers (e.g., AWS, Google Cloud) | Real residential devices and ISPs | Real residential ISPs, hosted on data center infrastructure |
| IP Rotation | Usually static; rotating options available | Automatic—changes per request or interval | None—fixed IP for weeks/months |
| Detection/Ban Risk | High (easily flagged by anti-bot systems) | Very low (mimics diverse real users) | Low (looks like a real, consistent user) |
| Typical Success Rate on Protected Sites | 40–60% (frequently blocked on sophisticated targets) | 95–99%+ (hardest to block at scale) | 90–95%+ (trusted like regular home connections) |
| Speed | Fastest (high-bandwidth servers) | Variable/slower (depends on real networks) | Very fast (close to datacenter performance) |
| Cost (Approximate, 2025) | Lowest ($0.50–$3 per proxy or cheaper in bulk) | Highest ($4–$15+ per GB or proxy) | Mid-range ($2–$10 per proxy/month) |
| Best For | High-speed tasks, budget projects, simple scraping | Large-scale web scraping, avoiding rate limits, maximum anonymity | Account management, ad verification, long sessions, sneaker/ticket drops |
| Main Drawbacks | Quick bans on major platforms, lower trust | Slower performance, more expensive, session interruptions from rotation | Limited supply in popular locations, higher cost than datacenter |
Why Static Residential Proxies Outperform Alternatives
These proxies shine in scenarios demanding consistency and low detection risk. Real-world advantages include:
- Exceptional Success Rates Residential IPs routinely hit 95–99% success on protected sites, while datacenter proxies often drop to 40–60% due to easy blacklisting.
- Persistent Sessions Keep the same IP across long tasks—no interruptions from rotation.
- Geo-Unlocking Power Appear as a local user to bypass region locks on streaming, e-commerce, or content platforms.
- Stronger Anonymity Ideal for competitive research or brand protection without exposing your origin.
- Account-Friendly Stability Perfect for managing profiles where sudden IP changes trigger flags.
Common Use Cases for Static Residential Proxies
1. E-Commerce & Sneaker Botting
Static residential proxies are the industry standard for “copping” limited-edition releases. Because they provide the speed of a data center but the identity of a real home user, they allow buyers to bypass “one-per-customer” rules and checkout faster than humanly possible without getting flagged.
2. Social Media & Account Management
Managing multiple profiles on platforms like Instagram, TikTok, or Facebook is risky.
- The Problem: Logging into 10 accounts from the same IP (or a rotating one) triggers “suspicious activity” alerts.
- The Solution: Assigning a dedicated static residential IP to each account mimics a single person consistently logging in from their home, preventing bans.
3. SEO Monitoring & Rank Tracking
Search engine results vary significantly by location. SEO professionals use static IPs to see “clean” localized results. Since the IP is static, it allows for consistent tracking of keyword rankings over time from a specific city or country without being skewed by personalized search data or IP rotation.
4. Ad Verification & Fraud Detection
Advertisers use these proxies to browse the web anonymously and verify that their ads are:
- Displaying in the correct geographical region.
- Not being placed on “junk” or fraudulent websites.
- Not being clicked on by malicious bots (by simulating a real residential user’s browsing journey).
5. Competitive Price Intelligence
In highly competitive markets like travel or retail, companies use static residential proxies to monitor competitor prices. Unlike data center IPs, which websites might “feed” fake pricing data to (price spoofing), static residential IPs see the same “real” prices that an actual customer sees.
Responsible Use vs Abuse: Behavioral Boundaries
The difference between responsible use and abuse of static residential proxies does not lie in the tool itself, but in how trust, persistence, and scale are applied. Static residential proxies were not inherently designed to bypass protections. They were designed to provide continuity, geographic accuracy, and stable connectivity. Problems emerge when these characteristics are deliberately pushed beyond the behavioral limits that platforms associate with real users.
To clarify this boundary, the distinction is best understood through observable behavior rather than declared intent.
Behavioral Comparison Matrix
| Dimension | Responsible Use | Abuse-Oriented Use |
| Request volume | Matches human pacing and session expectations | Exceeds realistic human throughput |
| Temporal patterns | Natural variability, pauses, and irregularity | Highly uniform or mechanically timed actions |
| Session persistence | Supports continuity without repetition abuse | Exploits long-lived trust for repeated bypass |
| Automation density | Automation assists limited workflows | Automation drives sustained, large-scale activity |
| Platform impact | Operates within system tolerance | Skews metrics, strains resources, or degrades fairness |
| Reliance on IP trust | IP is supplementary | IP is the primary evasion mechanism |
| Risk accumulation | Minimal behavioral anomalies | Compounding risk signals over time |
This distinction matters because modern platforms do not evaluate traffic in isolation. They evaluate patterns, consistency, and cumulative behavior.
When static residential proxies are used proportionately, they remain within the behavioral envelope that platforms were designed to accommodate. When abused, they systematically undermine trust models built around identity, fairness, and access control.
How Static Residential Proxies Are Exploited at Scale
Static residential proxies become problematic not because they are residential, but because they allow automation to inherit long-term trust signals that were originally meant for individual users. Once IP persistence and residential attribution are combined, they can be systematically reused to construct identities that appear stable, local, and legitimate over time. At scale, this enables abuse patterns that are difficult to distinguish from organic traffic using traditional controls.
The following categories illustrate how this exploitation typically unfolds, not as isolated incidents, but as repeatable operational models.
1. Automated Identity Creation and Trust Farming
One of the most common abuse patterns involves assigning a dedicated residential IP to each automated account. By distributing registrations across unique, long-lived residential IPs, bulk account creation no longer resembles a spike of suspicious activity. Instead, it appears as organic signups originating from different households and regions.
Once created, these accounts are gradually warmed up through low-risk actions, allowing them to accumulate trust before being used for fraud, manipulation, or resale. The abuse lies not in registration itself, but in the systematic manufacturing of perceived legitimacy.
2. Distributed Scraping and Credential-Based Attacks
Static residential proxies are frequently embedded into scraping frameworks and credential-stuffing tools. Rather than overwhelming a target from a single source, requests are distributed across hundreds or thousands of residential IPs, each operating at a low, human-like rate. Login attempts, data extraction, and probing activity blend into normal traffic patterns, evading rate limits and basic anomaly detection.
Persistence further compounds the problem, as repeated interactions from the same IP reinforce the illusion of a returning user rather than an automated process.
3. Advertising and Engagement Fraud
In advertising ecosystems, residential IPs function as a proxy for real user presence. Fraud operations leverage static residential proxies to generate clicks, impressions, and engagement events that appear geographically diverse and behaviorally consistent. From the platform’s perspective, this traffic often passes surface-level validation checks.
The result is not immediate disruption, but silent value erosion. Advertisers pay for activity that looks legitimate but produces no meaningful conversion, distorting performance metrics and undermining trust across the ecosystem.
4. Transactional and Financial Exploitation
In financial and transactional environments, geographic consistency is often used as a risk signal. By pairing stolen credentials or payment details with residential IPs that match the expected location, attackers increase the likelihood of successful transactions. Static IP persistence helps maintain session continuity, reducing friction during verification steps.
In other cases, residential IPs from permitted regions are used to bypass jurisdictional or regulatory access controls, allowing users to appear local where they are not.
5. Identity Reset and Access Evasion
Static residential proxies are also used to repeatedly reconstruct identity after enforcement actions. When accounts or devices are blocked, attackers simply re-enter systems using new residential IPs that carry no negative reputation. Because these IPs are not disposable and persist over time, they can be reused to rebuild trust from scratch. This cycle forces platforms into increasingly aggressive enforcement strategies, often at the expense of legitimate users.
6. Market Distortion and Resource Manipulation
In competitive or scarcity-driven markets, residential proxies enable unfair access at scale. By distributing actions across multiple trusted IPs, automated systems bypass purchase limits, reservation controls, and inventory protections. This allows a small number of operators to dominate limited resources while appearing indistinguishable from independent consumers. Similarly, distributed residential IPs are used to extract competitive data or influence market signals without triggering defensive thresholds.
Why Static Residential Proxy Abuse Is Hard to Detect
Each individual action enabled by static residential proxies appears reasonable in isolation. Sessions are stable. IPs are residential. Geographic signals align with expectations.
Traditional defenses evaluate traffic in snapshots. Static residential proxies exploit this limitation by distributing activity over time, space, and identity. No single request looks abnormal. No single session crosses obvious thresholds.
The abuse only becomes visible when signals are correlated across behavior, device, and historical interaction patterns. This is why static residential proxies represent a structural challenge rather than a tactical one. They exploit assumptions embedded in legacy trust models, where residential origin and IP persistence were once reliable indicators of legitimacy.
Case Study: When Static Residential Proxies Overwhelmed a Global Footwear Brand
The abstract risks of static residential proxy abuse become clearer when examined through real-world impact.
The Challenge: Drowning in Fake Traffic
As limited-edition drops moved online, the brand became a primary target for organized scalping groups. These groups deployed thousands of Static Residential Proxies to create fake accounts and secure items within seconds.
Impact: Real fans were frustrated, and business metrics were distorted. “We were drowning in fake account registrations… they created a constant cleanup burden,” noted the brand’s Director of Growth.
The Solution: Moving Beyond IP-Based Defense
In 2018, the brand partnered with GeeTest to fortify their high-risk touchpoints: logins, add-to-cart, and checkout flows.
Intelligent Detection: GeeTest’s AI engine analyzed behavioral patterns and device signals. It revealed a shocking truth: During peak release events, up to 99.9 percent of purchase attempts originated from automated systems operating behind static residential proxies. Individually, these sessions appeared normal. Collectively, they formed highly synchronized and non-human interaction patterns.
To preserve brand identity and user experience, protective challenges were introduced in a way that aligned with the product culture. Instead of generic friction, interactions were branded and contextual, allowing genuine users to proceed while automation was filtered out.
The Results
- Accuracy Boost: A 35% increase in detection accuracy, vaporizing automated raids.
- Financial Health: Chargebacks tumbled by 32.8%, and fake account creation was gutted by 90%.
- Real Growth: Genuine sign-ups surged by 28% in just three months, as real fans finally had a fair chance to shop.
Final Thought
This article shows that static residential proxies are not inherently malicious. However, residential attribution and IP persistence, once treated as core trust signals, can no longer function as standalone indicators of legitimacy.
By allowing automation to inherit credibility at scale, static residential proxies expose the limitations of network based controls. When abuse develops gradually and remains behaviorally consistent, IP focused defenses tend to fail quietly rather than through obvious disruption.
Effective mitigation does not begin with blocking proxy categories. It begins with recognizing that trust must be established through behavior, continuity, and historical context rather than network origin alone.
As automated abuse continues to evolve, the separation between infrastructure and intent is becoming a defining challenge for modern bot mitigation and fraud prevention.





