1. What is an Account Takeover (ATO) attack?
An ATO attack occurs when attackers use stolen or guessed credentials to take control of legitimate user accounts and operate as trusted users.
2. How does an ATO attack typically work?
ATO attacks progress in stages, from gaining initial access, to observing normal behavior, and finally exploiting the account for fraud or data theft.
3. What are the main technical methods behind ATO attacks?
Core methods include automated credential attacks, phishing and social engineering, session hijacking, and exploitation of application or API weaknesses.
4. What are the main impacts of account takeover attacks?
Core methods include automated credential attacks, phishing and social engineering, session hijacking, and exploitation of application or API weaknesses.
5. How can ATO attacks be detected effectively?
Detection relies on behavioral analysis, device recognition, login and location anomalies, account activity monitoring, and AI-driven risk scoring.
6. What is the key principle of preventing ATO attacks?
Modern ATO prevention focuses on adaptive, risk-based protection that increases attack cost while minimizing friction for legitimate users.
What Is an Account Takeover (ATO) Attack?
An account takeover attack occurs when an attacker gains unauthorized access to a legitimate user account and assumes control of it. The attacker typically does not exploit a vulnerability in the application itself. Instead, they exploit weaknesses in authentication by using stolen or guessed credentials.
Once access is obtained, attackers may change the account password, modify profile details, withdraw funds, make fraudulent purchases, steal personal data, or use the account to distribute spam and phishing links. Because these actions are performed through valid credentials, they often appear legitimate to basic security systems.
What makes ATO particularly dangerous is that it abuses trust. The account already belongs to a verified user, which means downstream systems may treat the attacker as a normal customer.
How Account Takeover (ATO) Attack Works?
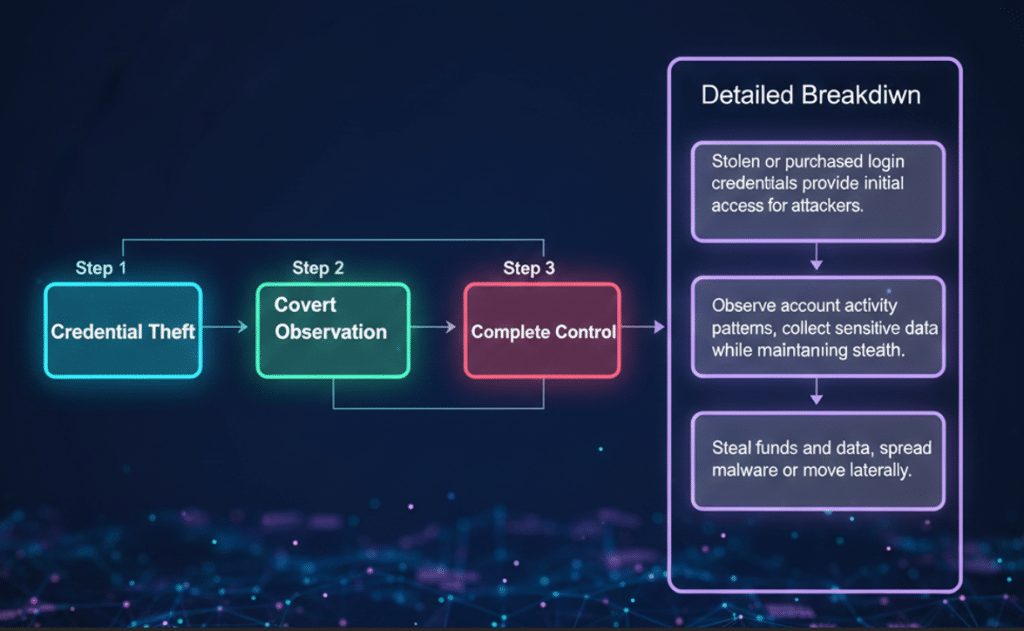
Account takeover fraud rarely happens in a single step. Instead, it develops gradually as attackers probe for weaknesses and expand their control over time. Criminals often begin with small-scale tests, attempting to access accounts using stolen or guessed credentials. Once a successful entry point is found, they escalate their activity until full control is achieved.
Understanding the progression of an ATO attack makes it easier to detect warning signs before serious damage occurs.
Stage 1: Gaining Initial Access
Most ATO incidents begin with compromised login information. Attackers may acquire credentials through deceptive emails, leaked databases, malicious software, or social manipulation tactics. In many cases, they purchase large collections of usernames and passwords from underground marketplaces and systematically test them across multiple platforms.
Because many users reuse the same credentials across services, even outdated breach data can remain effective long after it was first stolen.
Stage 2: Stealthy Observation
After successfully entering an account, attackers often avoid immediate action. Instead, they quietly monitor activity to understand how the account is normally used. They may review conversations, collect personal details, or copy messages to external inboxes.
This reconnaissance phase allows them to imitate legitimate behavior later, reducing the chance of triggering security alerts.
Stage 3: Taking Control and Exploitation
Once attackers feel confident they can operate unnoticed, they begin to abuse the account. This may involve transferring funds, sending fraudulent payment requests, accessing confidential information, or using the compromised account to spread malware or phishing messages.
In many cases, they modify account settings such as recovery emails, passwords, or permissions to prevent the rightful owner from regaining access. By the time suspicious behavior is noticed, the attacker may already have secured long-term control.
What Are the Entry Points and Execution Pathways?
The proliferation of digital communication and data storage creates multiple potential entry points for cybercriminals. User negligence regarding strong passwords further lowers the attack threshold—recent security analyses reveal that the most commonly used passwords remain simple numeric sequences or generic terms.
Attackers seek the simplest point of entry. Any personal information fragment used during login can become a gateway: email addresses, full names, dates of birth, or residential cities—all obtainable through basic research. Once primary communication channels are compromised, attackers can reset all associated settings: security questions, passwords, encryption parameters, and usernames. This comprehensive lockout can even make legitimate users appear suspicious during recovery attempts, as they can no longer provide updated account verification information.
What Are the Core Technical Methods of Account Takeover (ATO)?
1. Automated Credential Attacks
This path exploits human habits and scale to find easy entry points.
- Credential Stuffing: Using bots to test massive lists of leaked usernames and passwords across multiple sites, banking on the fact that people reuse login info.
- Password Spraying: A “low and slow” tactic that tests a few common passwords (e.g., 123456) against thousands of accounts to bypass lockout triggers.
- Brute-Forcing: High-frequency automated guessing of passwords, though less common now due to modern security lockouts.
2. Social & Technical Deception
This path targets the user directly through manipulation or “digital traps.”
- Spear Phishing: Highly customized, deceptive communications that trick specific users into revealing credentials or MFA codes.
- Social Engineering (OSINT): Researching public data and social media to guess security questions or gather enough “personal info” to impersonate the user to support teams.
3. Session & Token Hijacking
This path bypasses the need for a password entirely by stealing the “digital key” to an active session.
- Session Token Theft: Stealing active cookies via Cross-Site Scripting (XSS) or Man-in-the-Middle (MitM) attacks to impersonate the user.
- Cookie-Stealing Malware: Using specialized info-stealers or browser-targeting malware to export authentication tokens directly from a victim’s device.
4. System & Application Exploitation
This path targets the underlying code and infrastructure of the platform.
- Application Vulnerabilities: Exploiting flaws like SQL Injection or broken authentication logic to bypass login screens and access databases directly.
- API Insecurity: Targeting weak endpoints in mobile apps to manipulate account data or gain unauthorized access.
What Organizations are Impacted by Account Takeover Attacks?
Any organization with a customer-facing login portal is a potential target. However, threat actors strategically prioritize sectors where a single login provides immediate financial liquidity, redeemable assets, or high-value personal data.
| Sector | Primary Motivation | Key 2025–2026 Data Points |
| Financial & Fintech | Direct theft of balances, crypto, and wire fraud. | 122% YoY surge in ATO attacks; over $262M in losses from 5,100+ complaints in late 2025. |
| E-commerce & Retail | Stolen credit cards, loyalty rewards, and gift cards. | Ideal for scaled credential-testing due to massive daily login volumes. |
| Travel & Hospitality | Resale of premium accounts and travel points. | 56% increase in ATO attacks, driven by time-sensitive inventory and stored payments. |
| Healthcare | PHI (Protected Health Information) and billing fraud. | Consistently high breach rates due to the long-term resale value of health records. |
| Tech & SaaS | IP theft and supply-chain footholds. | 17% rise in attacks on software platforms, often linked to subscription abuse. |
Why These Organizations Are Prime Targets
Attackers look for environments where automation yields the highest return on investment:
- Monetizable Assets: Accounts with stored credit cards, crypto wallets, or redeemable points.
- Rich Data Sets: High concentrations of PII (Personal Identifiable Information) for medical identity theft or secondary fraud.
- Low-Detection Environments: High-traffic platforms where automated bot behavior can blend in with legitimate user logins.
- Security Gaps: Consumer-facing platforms often rely on weak MFA (like SMS) rather than phishing-resistant hardware keys.
Signs of Potential Account Takeover Fraud
Account takeover (ATO) is often stealthy, using stolen credentials or sessions. Spot these common red flags early to limit damage:
- Unusual Logins: Access from unknown devices, locations, IPs, or odd hours (e.g., late night or foreign country).
- Unauthorized Changes: Password, email, phone number, recovery options, or notification settings modified without your action.
- Security Alerts: Unexpected password reset emails, MFA code requests, new device verifications, or login notifications you didn’t trigger.
- Login Issues: Password suddenly invalid, repeated failed attempts followed by success, account locked, or unexpectedly logged out.
- Suspicious Activity: Small test transactions, unfamiliar transfers, added payees, redeemed rewards/gift cards, or strange messages sent from your account.
- Contact Feedback: Friends, family, or colleagues receiving odd requests for money, help, or spam you didn’t send.
- Other Red Flags: Surge in failed login attempts, geographically impossible quick location switches, or sudden drastic changes in account behavior.
For businesses/platforms (extra signals): Spike in customer complaints, anomalous sessions, deviation from historical user patterns.
What Are the Impacts of Account Takeover?
Once attackers gain unauthorized access to an account, the real damage begins. ATO enables direct exploitation, turning a foothold into financial theft, data misuse, or broader attacks. Impacts hit businesses and individuals differently but often overlap in severity.
Impacts on Businesses
Immediate Financial Loss: Hijacked corporate or brand accounts can be used to conduct fraud or scams within minutes. In the 2020 Twitter breach, attackers took control of verified business and celebrity accounts to promote a cryptocurrency scam, stealing over 120,000 USD in a matter of hours, demonstrating how quickly compromised accounts can be monetized.
Operational Disruption: ATO incidents often force organizations to suspend internal systems and launch emergency investigations. In 2022, Uber reported that an employee account was taken over using MFA fatigue techniques, granting access to internal tools and requiring temporary shutdowns of key services, disrupting normal business operations.
Supply Chain and Downstream Risk: When attackers compromise accounts within service providers or identity platforms, the impact extends to their customers. In 2023, Okta disclosed that attackers accessed its support system using stolen credentials, exposing data linked to more than 130 customer organizations and highlighting how one ATO event can cascade across multiple businesses.
Reputational Damage and Customer Trust Erosion: Publicly disclosed ATO incidents weaken confidence in a company’s ability to protect user identities. Loss of trust can result in customer churn, reduced platform usage, and long-term brand harm.
Regulatory and Compliance Exposure: If compromised accounts lead to personal data leakage, organizations may face regulatory investigations, contractual penalties, and increased compliance requirements under data protection laws.
Impacts on Individuals
- Financial Theft: Unauthorized transactions, drained balances, or redeemed rewards lead to direct losses, often in the thousands per victim in severe cases. U.S. consumers lost approximately $15.6 billion to ATO fraud in 2024.
- Identity Theft Expansion: Stolen personal data enables synthetic identities (blending real and fabricated info) for fake loans, credit lines, or other fraud, often undetected until credit scores are ruined or debt collectors appear.
- Secondary Attacks: Hijacked emails, social media, WhatsApp, or Instagram accounts turn into phishing hubs: attackers send “urgent” money requests or malicious links to contacts, exploiting trust for higher success rates (trusted-source messages often far more effective than generic phishing).
- Emotional & Time Burden: Victims face intense stress, time-consuming recovery (disputes, credit freezes, support calls), and “digital paralysis”—prolonged lockouts from primary email (the hub for banking, work, and social recovery), leaving them unable to prove identity or access services.
5 Methods for Detecting Account Takeover (ATO) Attacks
In 2026, ATO detection has shifted toward real-time, behavior-focused approaches rather than just post-login alerts. Attackers use stolen credentials or sessions to blend in, so effective methods rely on spotting deviations from normal patterns. Here are five proven, widely recommended methods:
1. Behavioral Anomaly & Biometrics Monitoring
Establish a baseline of each user’s typical actions (e.g., typing speed, mouse movements, navigation patterns, session duration) using behavioral biometrics or analytics. Flag deviations like sudden changes in behavior after login, unusual transaction velocity, or actions outside historical norms (e.g., accessing unfamiliar features). This catches post-compromise activity even when credentials are valid. Tools like machine learning models assign real-time risk scores to sessions.
2. Device Fingerprinting & Recognition
Track unique device attributes (browser config, screen resolution, fonts, plugins, hardware signals) to identify if a login comes from a known device or a new/emulated one. Combine with session intelligence to detect spoofed devices or sudden switches. New or unrecognized devices trigger alerts or step-up authentication—highly effective against malware/session hijacking.
3. Login & Location Anomaly Detection
Monitor for suspicious login signals: multiple failed attempts followed by success (credential stuffing), logins from impossible travel (geographically distant locations in short time), unfamiliar IPs/countries, TOR proxies, or data-center IPs. Geolocation + velocity checks (e.g., login from Hong Kong then immediately from Eastern Europe) are strong early indicators.
4. Account Activity & Change Monitoring
Watch for unauthorized modifications post-login: password/email/phone resets, new recovery options, added payment methods, forwarding rules, or disabled alerts. Also flag spikes in activity like rapid profile edits, bulk data access, or unusual transactions (e.g., small test buys before large drains). Real-time alerts on these changes catch persistence attempts.
5. AI/ML-Powered Risk Scoring & Real-Time Analysis
Use advanced fraud platforms that aggregate signals (device, behavior, location, velocity, historical data) into a dynamic risk score per session. High scores trigger challenges (CAPTCHA, step-up MFA) or blocks. This holistic approach excels at detecting sophisticated attacks like MFA fatigue bypass or session replay, outperforming rule-based systems.
These methods work best layered together in modern fraud platforms. For individuals: enable login alerts, review sessions/devices regularly, and use tools like Have I Been Pwned for exposure checks. For organizations: invest in continuous monitoring to shift from reactive to proactive detection—early flags often stop damage before monetization.
How To Prevent and Protect Against Account Takeover Attacks with GeeTest
In 2026, the battle against Account Takeover (ATO) has moved from static defense to Dynamic Adaptation. GeeTest has established itself as a leader in this space by moving beyond “blocking bots” to “increasing the cost of the attack.”
Here is how you can prevent and protect against ATO using GeeTest’s multi-layered security framework.
1. Deploying the “7-Layer Dynamic Security” Strategy
GeeTest’s Adaptive CAPTCHA (v4) doesn’t just show a puzzle; it initiates a 7-layer defense cycle that updates in real-time.
- The Strategy: During every defense cycle, the system can deploy up to 4,374 unique security strategies.
- The Result: This increases the cost of a bot attack by 3.7x, making large-scale credential stuffing (the primary precursor to ATO) financially unviable for attackers.
- Key Feature: Dynamic JS Obfuscation and Parameter Updates prevent hackers from reverse-engineering the protection or “faking” a successful solve.

2. Behavioral Verification: Beyond “What” to “How”
Traditional security checks what a user knows (password). GeeTest checks how they act.
- Behavioral Trajectory: It analyzes the millisecond-level mouse movements and click patterns. Bots, even sophisticated ones, lack the “micro-jitter” and organic acceleration of a human hand.
- Biometric Classification: GeeTest uses CNNs (Convolutional Neural Networks) and clustering models to distinguish human-like bot motions from actual humans, effectively neutralizing AI-driven bots designed to mimic people.
3. The “3 Shields” Framework: Holistic Identity Intelligence
GeeTest protects all access points (Web, App, API) by focusing on three distinct dimensions:
Behavior Verification: Stops automated scripts from simulating human actions.
Device Verification: Uses GCN (Graph Convolutional Networks) to identify “Cloud/Group Control” platforms. It creates a network of devices to spot when 500 accounts are suddenly logging in from the same “fingerprint.”
Identity Verification: Ensures that even if a password is valid, the context of the login (environment, IP reputation, and history) is secure.
4. Balancing Security with User Experience
One of the highest risks of ATO prevention is “Friction-Induced Churn.” If security is too hard, users leave.
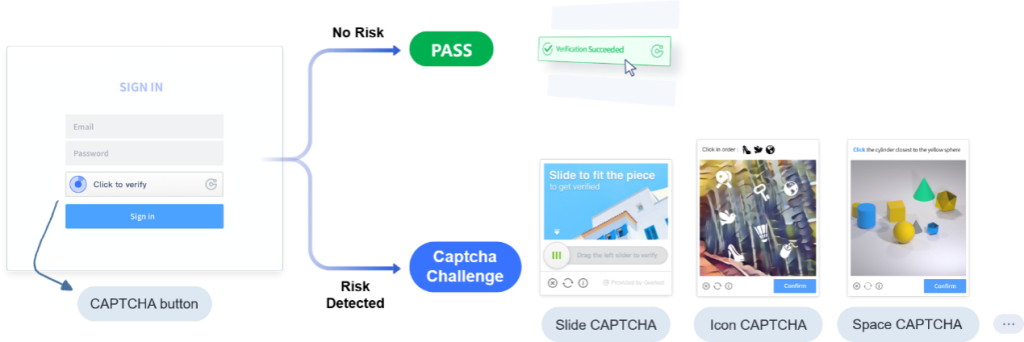
Intelligent Mode: GeeTest evaluates the risk level of the visitor before they see a challenge.
Low Risk: The user gets an “Invisible Probe” or a “OneTap Pass” (zero friction).
Medium/High Risk: The system triggers a more complex, anti-recognition challenge (Slide, Icon Selection, or Gobang).
Conclusion
Account takeover attacks succeed because they exploit legitimate credentials and trusted user identities, allowing malicious activity to blend in with normal behavior. As attack techniques evolve from simple credential abuse to session hijacking and social engineering, traditional perimeter-based defenses are no longer sufficient.
Effective protection now requires continuous verification of both identity and intent throughout the user journey. By combining behavioral analysis, device intelligence, and real-time risk assessment, organizations can detect subtle anomalies that signal compromise before financial loss or data exposure occurs.
Modern ATO defense is not about adding friction to every login, but about dynamically adapting security to risk. Platforms that adopt adaptive, behavior-driven protection can significantly reduce fraud while preserving user experience, turning account security from a reactive control into a proactive layer of trust.