Every online business faces the same tension. On one side, automated abuse continues to grow in scale and sophistication. On the other, users have less patience than ever for friction during login, registration, and checkout.
Traditional CAPTCHA challenges try to solve this problem by asking users to prove they are human. But visible challenges often punish legitimate users more than attackers. Bots adapt, humans abandon.
This is where Proof-of-Work CAPTCHA changes the conversation. Instead of asking users to solve a puzzle, it quietly asks their device to do a small amount of work in the background. For real users, the process is largely invisible. For bots operating at scale, it introduces a cost that cannot be ignored.
The real value of Proof-of-Work is not technical novelty. It is the ability to shift security pressure away from humans and onto automated abuse.
Why Traditional CAPTCHA Challenges Break the User Experience
Most CAPTCHA systems were designed for a simpler threat model. Ask a user to click images, drag a slider, or type distorted characters, and assume bots will fail. In reality, visible challenges introduce two problems at once. First, they interrupt legitimate users at critical moments, increasing friction and abandonment. Second, they create a predictable obstacle that attackers can study, outsource, or automate over time. As bots improve, visible challenges tend to escalate. Harder images, more steps, more interruptions. Each escalation further degrades user experience, while attackers continue to adapt. This dynamic leads to an uncomfortable outcome. CAPTCHA becomes increasingly visible to humans, while remaining manageable for determined automation.
How Modern Bots Really Operate
Contrary to popular belief, most bots do not aim to perfectly mimic human behavior. Precision is expensive. Scale is not. When sophisticated bypass techniques fail, attackers fall back on volume. They send large numbers of requests, knowing that even a small success rate can produce meaningful results. This pattern is common in credential stuffing, fake account creation, inventory abuse, and spam submissions. At this stage, the attacker’s advantage is not intelligence. It is throughput.
However, scale alone is not proof of abuse. Legitimate traffic spikes, batch operations, and API-driven workflows can also generate high request volumes. Scale becomes suspicious only when combined with abnormal behavioral, environmental, or interaction patterns. Any effective defense must therefore distinguish between legitimate high-volume activity and automation that persists through repeated failure.
Proof-of-Work CAPTCHA: Making Scale Expensive Again
The effectiveness of Proof-of-Work CAPTCHA is not based on obscurity or pattern recognition. It is rooted in a fundamental principle of cryptography: computational asymmetry. In simple terms, Proof-of-Work is designed so that solving a challenge is deliberately expensive, while verifying the solution is almost free. This imbalance is what makes large-scale automation economically unsustainable.
The Cryptographic Structure Behind Proof-of-Work
A Proof-of-Work challenge requires the client, whether a browser or a bot, to perform a small but measurable amount of computation before a request is accepted.
At a high level, the process works as follows:
- The server generates a unique challenge that includes a random value known as a salt and a predefined difficulty target. The difficulty defines how hard the task is, for example by requiring the output of a cryptographic hash to meet a specific condition.
- The client must then repeatedly combine the salt with a changing nonce and compute a hash until the result satisfies the difficulty target. This is a brute-force process by design. Each failed attempt costs CPU time, and there is no shortcut to guessing the correct nonce.
- Once a valid solution is found, the client submits it back to the server. Verification is trivial. The server only needs to run the hash calculation once to confirm the result.
Conceptually, the challenge can be represented as:
Hash(Salt + Nonce) < Difficulty Target
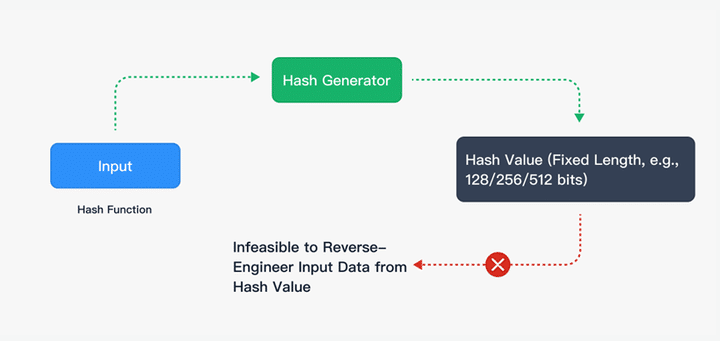
For a legitimate user, this computation is barely noticeable. For an attacker attempting thousands or millions of parallel requests, the cumulative cost quickly becomes prohibitive. This asymmetry is critical. Every request forces the attacker to pay a price in processing power, energy consumption, and infrastructure capacity, while the defender pays almost nothing.
Why Proof-of-Work CAPTCHA Stops Large-Scale Brute-Force Attacks
Brute-force attacks do not rely on sophistication at the individual request level. They rely on repetition. In credential stuffing, automated registration, and high-frequency abuse, attackers expect most attempts to fail. What matters is throughput. As long as each attempt remains cheap, scale compensates for low success rates.
Proof-of-Work directly targets this assumption. By enforcing a computational cost on every attempt, Proof-of-Work ensures that scale is no longer free. A single challenge may complete in milliseconds for a legitimate user, but thousands of concurrent challenges immediately translate into sustained CPU consumption, reduced parallelism, and higher infrastructure requirements.
As request volume increases, attackers face a linear increase in resource usage. To maintain the same attack speed, they must provision additional hardware, more compute instances, or more devices. At that point, the attack is no longer limited by detection accuracy, but by available processing capacity.
This is why Proof-of-Work is effective against brute-force abuse without relying on perfect classification. It does not need to determine intent at the first request. Instead, it ensures that persistence and repetition carry an escalating cost.
The Difference Between Traditional CAPTCHA and POW CAPTCHA
| Dimension | Traditional CAPTCHA | Proof-of-Work CAPTCHA |
| Core Question | Does this request look human? | Is the requester willing to pay a computational cost? |
| Primary Mechanism | Visual puzzles, sliders, text input, interaction challenges | Client-side cryptographic computation |
| User Interaction | Explicit and visible | Invisible or background-only |
| Impact on Legitimate Users | Interrupts critical flows such as login and checkout | Typically operates within normal latency budgets |
| Resistance to Brute-Force Attacks | Limited, attackers rely on scale or outsourcing | Strong, scale directly increases computational cost |
| Cost Distribution | Cost concentrated on human users | Cost concentrated on automated traffic |
| Attack Bypass Strategy | Outsourcing to solver services or automation optimization | Requires additional hardware and processing capacity |
| Scalability of Attacks | High, marginal cost per request remains low | Low, marginal cost increases linearly with volume |
| Server-Side Verification Cost | Low | Extremely low (constant-time verification) |
| Visibility to Users | High, challenges are noticeable and disruptive | Low, impact is only visible at scale |
| Adaptability | Escalates challenge difficulty, increasing friction | Adjusts difficulty dynamically without user involvement |
| Best Use Cases | Low-volume abuse, interaction-based verification | High-volume automation, brute-force and credential attacks |
Pros and Trade-offs of Proof-of-Work CAPTCHA
Advantages
- Economic deterrence against scale: Every request requires measurable computation, making high-volume attacks costly and inefficient. Particularly effective against brute-force attacks like credential stuffing and automated registrations.
- Minimal user friction: Operates in the background without requiring users to solve puzzles, click images, or perform additional steps.
- Resistant to outsourcing: Unlike traditional CAPTCHAs, the computational work is tied directly to client hardware, preventing easy offloading to third-party solving services.
- Lightweight server verification: Solutions can be verified with constant-time operations, allowing efficient scaling without adding backend load.
Trade-offs and Limitations
- Client performance variability: Devices vary widely in CPU power and energy efficiency; challenges calibrated for desktops may slow mobile or low-power devices if applied indiscriminately.
- Context insensitivity: High request volume alone is not a reliable indicator of abuse; legitimate traffic spikes and batch/API operations may trigger PoW unnecessarily.
- Not a standalone blocker: Proof-of-Work slows abuse rather than blocking it outright, so it should be combined with other verification signals for high-risk actions.
- Selective deployment required: Effectiveness depends on adaptive, risk-aware application; indiscriminate use can shift cost onto legitimate users.
From Always-On Challenges to Risk-Based Enforcement
Proof-of-Work CAPTCHA delivers its strongest value when applied selectively rather than uniformly. By adopting a risk-based and adaptive approach, systems can maintain a balance between security and user experience.
Instead of applying computational challenges to every request, Proof-of-Work is triggered only for traffic exhibiting suspicious patterns or elevated risk. Risk assessment considers multiple factors, including request frequency, behavioral anomalies, device environment, and geographic signals. This ensures that legitimate users are rarely impacted, while high-risk or abnormal traffic faces appropriate resistance.
Challenge complexity is dynamically adjusted according to the assessed risk. Low-risk users experience minimal or imperceptible computation, allowing them to complete logins, registrations, or transactions without noticeable delay. High-risk requests, on the other hand, encounter gradually increasing computational costs, making large-scale automation progressively more expensive and inefficient.
Repeated failures or continued suspicious behavior lead to further escalation. By progressively enforcing higher computational requirements, systems ensure that attackers incur greater costs over time without penalizing legitimate users. This adaptive enforcement works best when combined with environmental, behavioral, and traditional CAPTCHA signals, enabling a more accurate distinction between benign high-volume activity and automated abuse.
Overall, strategic deployment of Proof-of-Work allows online platforms to make high-volume attacks economically prohibitive while preserving seamless user experiences. Computation happens quietly in the background, ensuring security is enforced without disrupting legitimate traffic. This risk-aware model provides the foundation for how GeeTest implements Proof-of-Work in practice, combining dynamic activation with multi-layer verification to maintain robust security at scale.
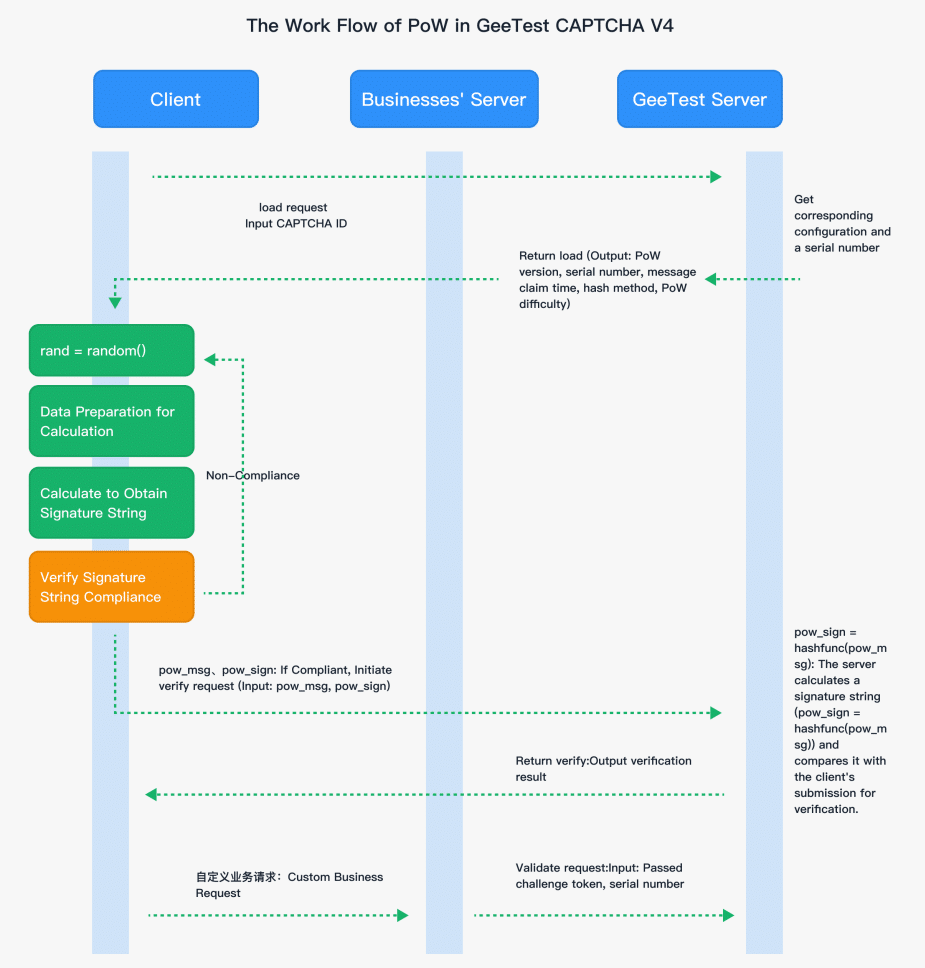
How GeeTest Uses Proof-of-Work in Practice
GeeTest CAPTCHA integrates Proof-of-Work as a core component within a broader, multi-layered verification framework. Rather than applying computational challenges uniformly, GeeTest evaluates traffic using a combination of behavioral analysis, environmental signals, and device context to determine when Proof-of-Work should be activated. This adaptive approach ensures that legitimate users proceed with minimal interruption, while attackers face escalating computational costs.
When traffic patterns indicate abnormal behavior, such as repeated failed login attempts, rapid registration submissions, or high-frequency API requests, Proof-of-Work challenges are introduced dynamically. The difficulty of these challenges is adjusted in real time according to the assessed risk, making each automated attempt progressively more resource-intensive. By enforcing computational cost selectively and adaptively, GeeTest effectively discourages high-volume automation without impacting ordinary users.
In addition, GeeTest combines Proof-of-Work with other verification mechanisms, including image-based challenges, client-side dynamic verification, and environmental risk signals. This multi-layered approach ensures resilience even if individual defenses are partially bypassed. Every request requires a measurable investment from the client side, while server-side verification remains lightweight and efficient.
Through this implementation, Proof-of-Work remains largely invisible to legitimate users. They experience smooth, uninterrupted login, registration, and transaction flows, while attackers attempting to scale their operations encounter rapidly compounding costs in processing power, energy, and infrastructure. This selective and adaptive strategy demonstrates how Proof-of-Work can be deployed effectively in real-world scenarios, achieving both security and usability objectives.
Conclusion
Proof-of-Work CAPTCHA reshapes the economics of automated abuse by attaching a real computational cost to every request. For legitimate users, the impact remains minimal and largely invisible. For attackers operating at scale, that cost compounds quickly, constraining throughput and eroding the viability of brute-force automation.
At the same time, Proof-of-Work is not a standalone solution. Applied indiscriminately, it can introduce unnecessary latency for low-power devices or legitimate high-volume workflows. Its effectiveness depends on when and how it is enforced, not simply on its presence.
The most effective deployments treat Proof-of-Work as a selective pressure rather than a universal gate. When activated dynamically and combined with behavioral and environmental signals, it delivers strong protection while preserving user experience. In this role, Proof-of-Work becomes not just a defensive mechanism, but a practical tool for balancing security, scalability, and usability.