Based on the presentation delivered by GeeTest security expert Liu Haozhen in DataFun x GeeTest on May 15th, 2021.
On May 15th, the DataFun Summit on the topic of fraud prevention was held within Chinese cybersecurity community. The leader of GeeTest Security Lab Liu Haozhen and Senior algorithm engineer Hu Yiran brought GeeTest’s practices and experience to the forums and led meaningful discussions with the experts from tech giants including Tencent, Bilibili, Beike, Douyu TV, JD, and ByteDance, etc. Above 3,000 people, most of whom are engineers joined the webinar.
The Chief Information Officer from Jimu App emphasized the importance of knowing the fraud practices happening in their end-user communities where 40% of their team resources have been distributing. GeeTest follows the same philosophy when it concerns studying online threats.
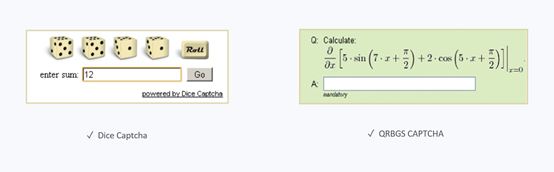
The presentation was started by introducing the history and the evolution of CAPTCHA, through which we learned that there are two basic factors of CAPTCHA, security and user friction. Generally, the more secure a CAPTCHA is, the more difficult it is for people to pass. The below two pictures are examples of secure CAPTCHAs that even humans cannot pass.
Researchers have been trying to find approaches to tell humans and machines apart through data analysis from different dimensions. CAPTCHA is one of the approaches that is developed based on behavioral analysis. GeeTest CAPTCHA 1.0, which is widely known as the slide puzzle CAPTCHA, can distinguish bots from humans as the early-stage bots cannot perform complicated behavior as humans do, like matching the puzzle piece. By amassing data on behavior patterns, researchers developed the next generation of CAPTCHA, GeeTest 2.0, with a behavior analysis algorithm embedded.
GeeTest 3.0 introduced an intelligent mode. The inspection finishes even before the user clicks the CAPTCHA. The intelligent mode can identify bots from the behavioral data like mouse tracking, mouse hover time, browser features, and so on. If the analysis proves the end user is good, it will let them pass without prompting any CAPTCHA challenge at all.
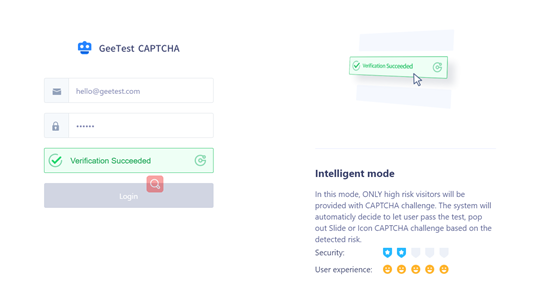
Unlike the traditional text CAPTCHA, the CAPTCHA based on behavioral data analysis is another world as its background mechanism keeps inspecting behavioral biometrics data even before the user clicks the CAPTCHA button. For CAPTCHAs, either legacy text CAPTCHA or modern CAPTCHA, it always takes a period to accumulate a sufficient amount of data feeding and training the machine learning model, so that humans and bots can be accurately distinguished. The process dramatically reduces user friction, meanwhile, guarantees security and data privacy.
In the second part of the presentation, Haozhen explained the three major roles that GeeTest CAPTCHA plays in fraud prevention.
Increase the Hacking cost
CAPTCHA can be implemented at the forefront of use cases like Sign-in, retrieving passwords, order placement, etc as a gatekeeper to mitigate threats like credential stuffing, brute-force attacking, etc. The continually evolving strategies dramatically increase the hacking cost.
Act Upon Malicious Traffic
Now many websites and mobile apps have built up their cybersecurity platforms. Because it is much easier and more efficient for the companies to build their own systems out of the understanding of their real business. For those who need to make a judgment about a machine user, a less-friction tool is a great choice to decrease the false positives. GeeTest CAPTCHA can be flexibly integrated into the client’s system and enable them to choose different CAPTCHA forms for specific situations.
Risk Analysis
GeeTest CAPTCHA can help collect information in various dimensions through different CAPTCHA forms. For example, slide puzzle CAPTCHA can collect users’ slide trails. Icon CAPTCHA and Space CAPTCHA can collect users’ click trails and click results. These data can enrich the analysis perspectives.
The third part of the presentation was about the threats that GeeTest CAPTCHA is facing.
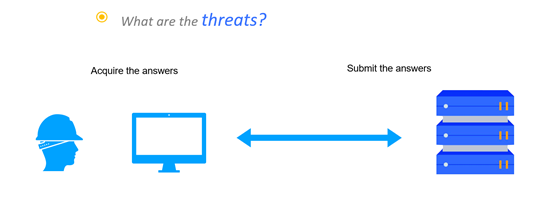
Having studied attacking patterns for years, we summarized how CAPTCHA is typically solved into two aspects. One is how the attackers acquire answers to CAPTCHA challenges, the other is how they submit those answers. Image recognition algorithms and virtual sweatshops are the common methods to be used for acquiring the answers. Afterward, the answers have to be submitted to the server and the CAPTCHA is bypassed once the submitted answer matches the one that severs side needs. This process is done in the form of an HTTP request. Attackers usually use emulators like Selenium or write a scripting file to make API calls.
Later Haozhen mentioned the four aspects that should be measured when we evaluate the security of a CAPTCHA, which are :
infrastructure security,
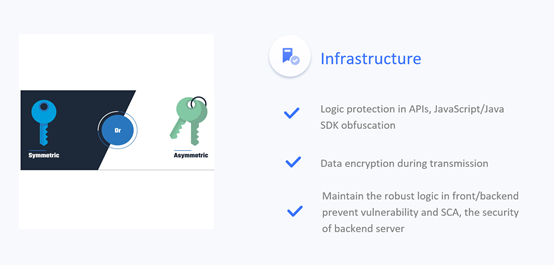
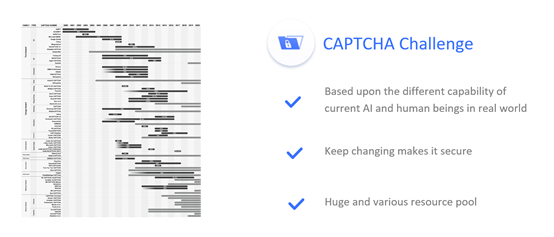
how secure the CAPTCHA challenge form is,
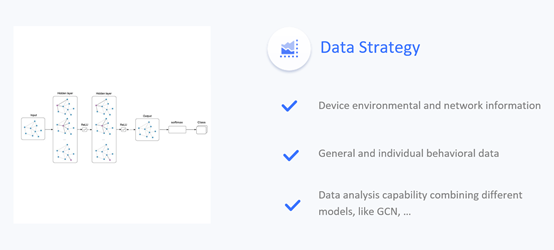
the strong algorithm behind the scene,
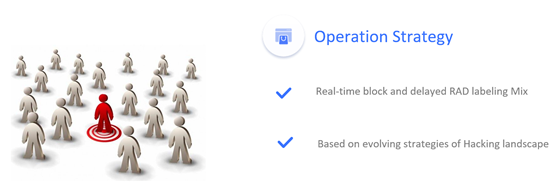
and supporting operation strategies to defeat any possible changes.
Finally, he shared his thoughts upon the possible directions of future CAPTCHA or verification ways, and also topics related to privacy respected policies, and the social values that a CAPTCHA can bring to human beings. In short term, CAPTCHA cannot be completely superseded by any other tool. User interaction is always the frontline during the battle with cyber frauds. The industry will advance in exploring better AI algorithms to tell humans and bots apart from ethically respecting user privacy.