As digital transactions grow in both volume and importance, identity verification has become one of the most critical components of cybersecurity. In 2025, SMS One-Time Passwords (OTP) continue to play a major role in protecting accounts, transactions, and sensitive operations.
Despite the rise of biometric authentication and app-based authenticators, SMS OTP holds a unique position because of its simplicity, universality, and accessibility—every mobile phone can receive a text message.
But widespread adoption also means attackers see SMS OTP as a lucrative target. One of the most widely used defenses for protecting SMS OTP systems has been CAPTCHA. For years, CAPTCHA was effective at preventing bots from abusing OTP request endpoints. Yet as automation and artificial intelligence have advanced, traditional CAPTCHA is no longer strong enough.
This blog will explore what SMS OTP is and how to protect it effectively in today’s evolving security landscape.
Key Features
- What SMS OTP is and why it matters.
- The main threats to SMS OTP security in 2025.
- The historical role of CAPTCHA in SMS OTP protection.
- Why traditional CAPTCHA fails against modern threats.
- The emergence of advanced CAPTCHA solutions as a necessity.
- Best practices for ensuring strong SMS OTP security in the future.
What is SMS OTP?
Definition and Function
SMS OTP stands for Short Message Service One-Time Password. It’s a temporary, randomly generated code sent via text message to a user’s registered phone number. The user enters this code into the application or website to prove they are the rightful account holder.
When a user initiates a login or transaction that requires additional verification, the system generates a unique OTP and sends it to the registered mobile number. The user must then enter this OTP within the specified time frame to complete the authentication process. This process ensures that only the person in possession of the registered mobile device can access the account or complete the transaction, significantly reducing the risk of unauthorized access. By leveraging the unique association between a user and their mobile device, SMS OTP provides a practical and effective layer of security.
Typical Use Cases
- Login Authentication: A user enters their password and is then asked to provide an SMS OTP for added security.
- Transaction Confirmation: Banks and payment providers send OTPs to verify high-value or sensitive transactions.
- Password Reset and Account Recovery: OTPs confirm that the account owner has access to the registered phone number.
- Regulatory Compliance: In many regions, OTP is mandated as part of strong customer authentication.
Why SMS OTP Remains Widespread
SMS OTPs are convenient because they leverage the ubiquity of mobile phones. Almost everyone carries a mobile phone, making SMS OTP a practical choice for authentication.
- Ubiquity: Works on nearly every mobile device.
- Accessibility: Users do not need to install apps or carry additional tokens.
- Ease of Understanding: Simple concept for users—receive a code, enter it.
- Low Integration Cost: Businesses can implement SMS OTP through standard messaging gateways.
Even though newer technologies exist, SMS OTP remains an essential authentication tool in 2025.
Weaknesses of SMS OTP
- Vulnerable to SIM swap attacks.
- Can be intercepted through phishing.
- Not encrypted once delivered to a phone’s messaging app.
- Most importantly, OTP request endpoints can be abused by automated attacks unless additional safeguards are in place.
SMS OTP Security: Key Threats in 2025
While SMS OTPs add a vital layer of security, they are not impervious to threats. As we approach 2025, cybercriminals are becoming increasingly sophisticated, necessitating enhanced security measures. Understanding the potential vulnerabilities and implementing robust security protocols is essential to maintaining the integrity of SMS OTPs.
SIM Swap Attacks
Attackers trick mobile carriers into transferring a phone number to a new SIM card, enabling them to intercept OTPs. This threat has become more prevalent with the rise of social engineering tactics, where attackers gather personal information to impersonate victims convincingly. Protecting against SIM swapping involves not only securing mobile carrier processes but also educating users on safeguarding personal information.
Phishing
Cybercriminals may attempt to deceive users into revealing their OTPs through fake websites or messages. These attacks often involve creating websites or emails that closely mimic legitimate services, tricking users into entering their OTPs and other sensitive information. To counter phishing, businesses must implement sophisticated anti-phishing technologies and educate users on identifying suspicious communications.
Interception Attacks
Hackers intercept communications between a user and a website, potentially capturing OTPs in transit. This type of attack can occur when users connect to unsecured networks or when hackers exploit vulnerabilities in communication protocols. Ensuring end-to-end encryption and utilizing secure transmission channels are crucial steps in mitigating the risk of man-in-the-middle attacks.
The Impact of Data Breaches
Data breaches can significantly compromise SMS OTP security by exposing user information that aids attackers in crafting targeted attacks. When user data is leaked, it can be used to execute more convincing phishing or social engineering attacks. Ensuring robust data protection measures and rapid response protocols in the event of a breach is essential to maintaining the integrity of SMS OTP systems.
Automated Attacks – The Most Critical Challenge
The most disruptive threat today is automation. Automated attacks exploit OTP flows at scale, including:
- Credential Stuffing with OTP Testing: Bots use stolen username–password pairs, then request OTPs to verify valid accounts.
- Brute Force OTP Entry: Bots rapidly test possible OTP values in input fields.
- SMS Bombing: Attackers flood OTP request endpoints to exhaust resources or harass users.
- Mass Exploitation: Botnets can trigger thousands of OTP requests per minute, overwhelming systems.
These automated threats scale far beyond what human attackers could manage. They exploit the fact that OTP endpoints, if unprotected, are open to anyone.
This is where CAPTCHA historically became an important line of defense.
CAPTCHA as a Shield for SMS OTP Security

The Original Purpose of CAPTCHA
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) was designed to distinguish human users from bots. By asking users to solve a puzzle, it prevents automated systems from abusing services.
How CAPTCHA Protects OTP Flows
For OTP flows, CAPTCHA has been used in three main ways:
- It blocks bots from requesting OTP codes automatically.
- It prevents automated brute-forcing of OTP entry fields.
- It mitigates credential stuffing campaigns by adding friction.
Historical Strengths of CAPTCHA
- Effective Against Early Bots: Traditional CAPTCHA stopped simple automated scripts.
- Easy to Deploy: APIs like reCAPTCHA made integration quick.
- Cost-Effective: Free or low-cost solutions were widely available.
- Widely Adopted: CAPTCHA became the default choice for businesses securing OTP endpoints.
For nearly a decade, adding CAPTCHA was enough to stop large-scale automation against OTP systems.
Why Traditional CAPTCHA Fails in 2025
As technology evolves, so do the tactics employed by cybercriminals. Emerging threats, such as AI-driven attacks or deepfake technologies, pose new challenges to SMS OTP security. The effectiveness of traditional CAPTCHA has been steadily eroded.
1. AI and Machine Learning Solvers
Today’s bots can solve text-based CAPTCHAs and image recognition challenges with accuracy levels exceeding human performance. Automated CAPTCHA-solving services are cheap, making bypass trivial.
2. User Experience Problems
- Annoying Puzzles: Endless image grids frustrate users.
- Mobile Limitations: Solving CAPTCHAs on a smartphone is cumbersome.
- High Abandonment: Users often quit when confronted with too many puzzles.
3. Accessibility Concerns
Users with visual impairments or other disabilities struggle with traditional CAPTCHAs, excluding legitimate customers.
4. Static Design
Legacy CAPTCHAs rely on fixed challenges. Attackers adapt once, and the puzzle type becomes obsolete.
The Impact on SMS OTP Security
For SMS OTP systems, this means:
- Automated bots slip through defenses.
- Legitimate users abandon flows due to poor experience.
- Security gaps remain, while conversions suffer.
The conclusion is unavoidable: traditional CAPTCHA is not sufficient to protect SMS OTP in 2025.
Advanced CAPTCHA: A Necessary Evolution for SMS OTP Security
To counter modern automation, a new generation of CAPTCHA has emerged.
What Makes CAPTCHA “Advanced”?
- AI-Driven Detection: Uses real-time machine learning to analyze behavior and context.
- Behavioral Biometrics: Monitors how a user interacts with a site (mouse movement, scrolling, touch dynamics).
- Adaptive Challenges: Applies different verification levels depending on risk profile.
- Low User Friction: Legitimate users often pass without solving any visible puzzle.
- Future-Proof: Continuously updated to match evolving bot capabilities.
- Professional Support: Enterprises gain access to expert teams that help respond to new attack vectors quickly.
Benefits of SMS OTP Security
- Blocks automated OTP abuse with AI-powered detection.
- Preserves user experience by minimizing interruptions.
- Adapts to new threats rather than relying on static puzzles.
- Provides enterprise-grade reliability with dedicated support.
In the context of SMS OTP, advanced CAPTCHA ensures that only real users can request and submit OTPs, while automated botnets are stopped at the gate.
Traditional CAPTCHA vs. Advanced CAPTCHA
The message is clear: businesses that continue to rely on traditional CAPTCHA are exposing themselves to fraud and user dissatisfaction.
| Feature | Traditional CAPTCHA | Advanced CAPTCHA |
|---|---|---|
| Security | Bypassed by AI solvers and cheap CAPTCHA farms | AI-driven, adaptive, resilient |
| User Experience | High friction, repetitive puzzles | Low friction, mostly invisible |
| Accessibility | Poor support for disabled users | Designed for inclusivity and mobile |
| Adaptability | Static challenges | Dynamic, evolving |
| Effectiveness | Weak against automated attacks | Strong, tailored for modern threats |
Enhancing OTP Fraud Prevention with GeeTest Solutions
For businesses, safeguarding against OTP fraud—particularly SMS OTP abuse—requires more than just basic authentication methods. A comprehensive security framework must integrate multiple layers of defense to effectively block automated and fraudulent activities. The GeeTest Bot Management Platform combines Behavior Verification, Device Fingerprinting, and a Business Rules Decision Engine to deliver advanced protection against attackers.
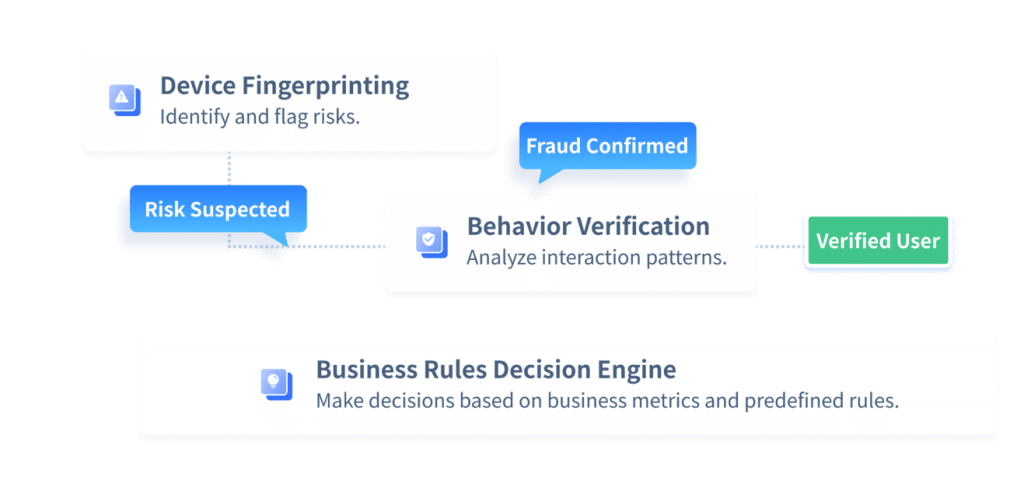
Behavior Verification
By continuously monitoring user interactions, behavior verification identifies anomalies that may signal fraudulent activity. Patterns such as repeated failed login attempts, unusually rapid input speeds, or access from unfamiliar environments trigger risk alerts. GeeTest’s behavioral analytics build detailed user interaction profiles, allowing abnormal activities to be detected at an early stage. When deviations are observed, the system can introduce step-up verification to silently block malicious attempts, all while keeping the experience smooth for legitimate users. This proactive approach minimizes fraud risk without adding unnecessary friction.
Device Fingerprinting
GeeTest Device fingerprinting enhances OTP security by uniquely identifying devices that access a system. It analyzes hardware and software attributes—such as browser type, operating system, timezone, plugins, and subtle rendering behaviors—to create a persistent digital “fingerprint.” By associating user accounts with trusted devices, businesses can quickly detect suspicious logins from unrecognized endpoints and take appropriate action. This extra layer of verification makes it significantly harder for attackers to reuse stolen credentials or OTPs across unauthorized devices.
Geo-Location Tracking with Business Rules
When combined with GeeTest’s Business Rules Decision Engine, geo-location tracking adds a powerful contextual layer to OTP protection. By assessing the geographic origin of login attempts, organizations can spot access from high-risk regions or locations inconsistent with a user’s typical behavior. Customizable policies allow businesses to block, challenge, or flag activity based on location-based parameters. This ensures OTPs are only validated when accessed from trusted regions, effectively reducing exposure to global fraud networks.
Together, these capabilities form a multi-dimensional defense strategy. Instead of relying on static, single-layer protections, GeeTest enables businesses to detect and mitigate fraud in real time, protecting both users and systems from sophisticated OTP abuse.
Looking Ahead: The Future of SMS OTP Security
As we look towards 2025, the landscape of digital security will continue to evolve. The integration of AI-driven security solutions, advanced CAPTCHA technology, and robust fraud prevention techniques will be essential in maintaining the integrity of SMS OTPs. By staying informed and proactive, businesses and users alike can navigate the challenges of the digital age with confidence.
The Growing Role of AI in Security
AI’s role in security will continue to expand, offering new opportunities for identifying and mitigating threats. As AI algorithms become more sophisticated, they will be able to analyze increasingly complex data sets, providing deeper insights into potential vulnerabilities. Businesses that embrace AI-driven security solutions can expect enhanced protection and a competitive advantage in safeguarding their digital assets.
Emerging Technologies and Their Impact
Emerging technologies, such as blockchain and quantum computing, have the potential to revolutionize SMS OTP security. Blockchain’s decentralized nature can provide a secure and transparent method for managing and verifying OTPs, while quantum computing could redefine encryption standards. Staying informed about these technologies and exploring their applications in security will be crucial for businesses looking to stay ahead of the curve.
The Importance of Continuous Innovation
In an ever-changing digital landscape, continuous innovation is key to maintaining effective security measures. Businesses must remain agile and responsive, regularly updating their security protocols to address new threats and challenges. By fostering a culture of innovation and collaboration, organizations can develop cutting-edge solutions that protect their users and maintain the trust and confidence of their customers.
Conclusion
SMS OTPs remain a crucial tool in the arsenal of digital security. However, as threats evolve, so too must the measures we take to protect them. By leveraging AI, advanced CAPTCHA solutions, and comprehensive security frameworks, we can ensure that SMS OTPs remain a secure and reliable method of authentication in 2025 and beyond.
Remember, the key to staying secure lies in continual adaptation and awareness. By embracing technological advancements and prioritizing user education, businesses and individuals can confidently navigate the complexities of the digital world, safeguarding their information and privacy.
FAQ
Why is SMS OTP still used in 2025?
Because it’s simple, works on any phone, and doesn’t need extra apps or devices.
What are the main risks of SMS OTP?
SIM swap, phishing, message interception, and especially automated bot attacks.
What does CAPTCHA do for OTP security?
It blocks bots from abusing OTP requests and brute-forcing OTP inputs.
Why is traditional CAPTCHA no longer enough?
Modern bots and AI can solve old CAPTCHAs easily, and they frustrate real users.
What is Advanced CAPTCHA?
A smarter, AI-powered CAPTCHA that detects bots based on behavior and risk signals.
How is Advanced CAPTCHA better for users?
Most real users don’t even see a puzzle—it works silently in the background.
How does GeeTest help with OTP security?
Through behavior verification, device fingerprinting, and business rules decision engine.